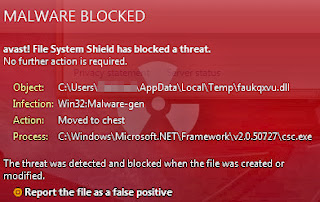
Win32: Somoto-J (PUP) is described as a destructive Trojan virus that can be lurked into random computers easily, especially for those are short of high security protection. Usually, computer users may realize the existence of Win32: Somoto-J (PUP) virus by having a full scan with anti-malware tools on computer. As one member of Win32 threats, it may bring up related viruses such as Win32: Somoto F-(PUP) and Win32: SearchProtect-C (Adw) on PC.
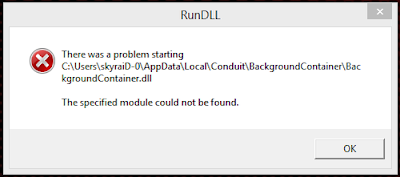
The Win32: Somoto-J (PUP) is generally bundled with adware program. Once the malicious adware applications permeates onto computer; the Win32: Somoto-J (PUP) virus as well as other potential threats can be activated automatically. Without timely removal, the Win32: Somoto-J (PUP) virus can take advantage of system bugs and open a backdoor for remote hackers. No doubts that your computer and privacy will be under high-risk due to the presence of Win32: Somoto-J (PUP) virus.
Hence, it is absolute that the Win32: Somoto-J (PUP) virus should be removed once being detected for the sake of preventing its worse damage.
Dangerous Win32: Somoto-J (PUP) on PC
- Win32: Somoto-J (PUP) installs without your consent
- Win32: Somoto-J (PUP) can open doors for other types of spyware/adware
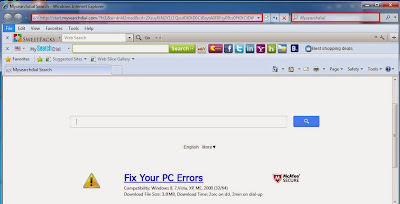
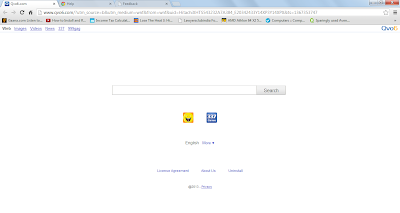
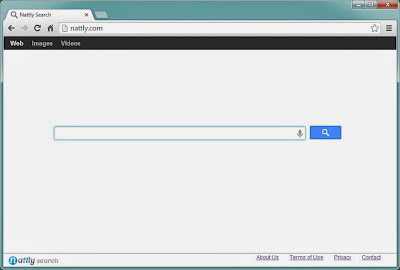
- Win32: Somoto-J (PUP) may hijack, redirect and change your browser
- Win32: Somoto-J (PUP) displays annoying pop-ups while you surf the web
- Win32: Somoto-J (PUP) compromises your privacy and security
- Win32: Somoto-J (PUP) is difficult to uninstall
Manually remove Win32: Somoto-J (PUP) step by step
Even though you have the top antivirus program installed, the Win32: Somoto-J (PUP) virus still gets through without your consent. You may ask why. I should say there is actually no such thing as perfect protection. Virus is created every day. Such virus like the Win32: Somoto-J (PUP) is designed to have been changed the code so antivirus can’t keep up. Once executed, Win32: Somoto-J (PUP) virus can disable your security tool. In such circumstance, manual removal is required.
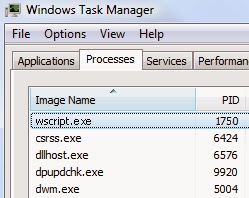
1. Launch the Task Manager by pressing keys “CTRL + Shift + ESC”, search for Win32: Somoto-J (PUP) processes and right-click to end them.
2. Show hidden files of Win32: Somoto-J (PUP)
a. Open Folder Options: clicking the Start button> Control Panel> Appearance and Personalization, and then clicking Folder Options. After that, click the View tab.
b. Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
3. Get rid of the following files created by Win32: Somoto-J (PUP):
%Windows%\system32\consrv.dll
Counter-Strike Source.exe
9719831.exe
verupd.exe
wb.exe
system.exe
Windows.exe
WUDHost.exe
svchost.exe
win32rundll.exe
dwm.exe
audiohd.exe
waudiohd.exe
4. Open Registry Editor (in Windows XP, go to Start Menu, run, type in “Regedit” and press OK; in Windows 7 & Windows Vista, go to Start menu, Search, type in “Regedit”), find out the following Win32: Somoto-J (PUP) registry entries and delete:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\ Win32: Somoto-J (PUP)
Please note, this is a self help manual guide; you need to possess sufficient skills about dealing with registries entries, dll. files and program files, you need to be very careful to move on every step. Can’t uninstall Win32: Somoto-J (PUP) yourself? Please click on VilmaTech 24/7 Online Computer Experts for help, you problem will be fixed immediately.