Meanwhile, the Trojan.BitcoinMiner virus is also diffused by some malicious websites or unknown attachments in spam email. As soon as being installed on PC, this type of Trojan virus would start to make changes on system secretly. Typically, it will modify the work of system boot sector, which take control of operating system’s bootloader. As a result, it could be loaded up automatically whenever users start PC. Afterwards, the Trojan.BitcoinMiner virus may exploit system bugs and then install additional threats onto compromised machine, including Browser hijack virus, worms or fake antivirus application. This will directly make worse results on affected computer. Thereupon computer users need to remove Trojan.BitcoinMiner immediately once being informed of its existence to avoid further damage.
How to Remove Trojan.BitcoinMiner Completely
1. Safe Mode with Networking
For Windows 7, XP & Vista
Reboot your computer into "safe mode with networking" by constantly tapping F8 key before Windows is launched.
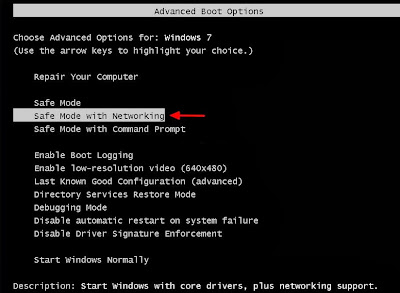
For Windows 8 users:
- Press the Ctrl+ Alt+ Del to start. And then hold down the “Shift” key on the keyboard and at the same tine click on “Shut down” button once on the bottom right corner of the page.
- You will get this Choose an option Screen after you clicked on See advanced repair options. Now you will need to click on the Troubleshoot option to continue.
- When you get on this Troubleshoot Screen, you can see there are three options listed, please click on or select the Advanced Options.
- Now you are at the Windows Startup Settings option, by the looks of things we were never meant to find Safe Mode With Networking, you are required to click on Restart Button to continue.
- When you are at the Advanced Boot Options, use the arrow keys to highlight the “Safe Mode with Networking” option, and then press ENTER or Press a number to choose from the option, if we now want to enable safe mode with networking, then press 5.
2. Show hidden files of Trojan.BitcoinMiner
- Click on the Start button and then on Control Panel
- Click on the Appearance and Personalization and go to Folder Options.
- Click on the View tab in the Folder Options window
- Choose the Show hidden files, folders, and drives under the Hidden files and folders category. Select OK at the bottom of the Folder Options window.
3. Stop Trojan.BitcoinMiner running processes in the task manager first.
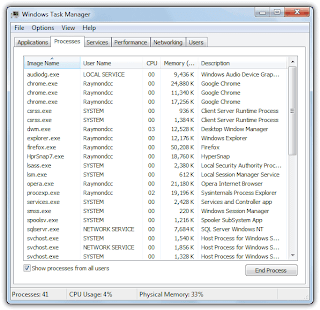
4. Remove all Trojan.BitcoinMiner registry entries listed here:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[RANDOM]”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[RANDOM].exe”
5. Remove these associated Files on your hard drive:
%Documents and Settings%\[UserName]\Application Data\[random]
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe
How to Prevent from Trojan.BitcoinMiner
- Use a firewall to block all incoming connections from the Internet to services that should not be publicly available. By default, you should deny all incoming connections and only allow services you explicitly want to offer to the outside world.
- Enforce a password policy. Complex passwords make it difficult to crack password files on compromised computers. This helps to prevent or limit damage when a computer is compromised.
- Ensure that programs and users of the computer use the lowest level of privileges necessary to complete a task. When prompted for a root or UAC password, ensure that the program asking for administration-level access is a legitimate application.
- Disable AutoPlay to prevent the automatic launching of executable files on network and removable drives, and disconnect the drives when not required. If write access is not required, enable read-only mode if the option is available.
Note: The above mentioned Trojan.BitcoinMiner manual removal process is really risky and cumbersome which should be handled with adequate expertise skills. So, this removal job is only suggested for those advanced PC users, because any mistake of removing critical files and registry entries will lead to your computer crash terribly.
To get your PC problem resolved successfully within only a short period of time, you’d better consult VilmaTech Computer Experts 24/7 Online from Global PC Support Center to help you remove Trojan.BitcoinMiner from your PC completely.



Hey. Thanks for providing those guidelines on how to remove this malware. I did a recent evaluation on this malware myself and I pretty much learnt a lot about it and so I was moved to write a post about it. Most people would opt for a manual method to remove this malware but I don't think that's possible, at least not in the assessment I did. BitcoinMiner showed no trace that it was installed. In fact, the only way I knew that the malware was present was after I used a detection tool to detect it. This malware operated in the shadows and definitely wanted to remain unseen.
ReplyDeleteAre you willing to know who your spouse really is, if your spouse is cheating just contact cybergoldenhacker he is good at hacking into cell phones,changing school grades and many more this great hacker has also worked for me and i got results of spouse whats-app messages,call logs, text messages, viber,kik, Facebook, emails. deleted text messages and many more this hacker is very fast cheap and affordable he has never disappointed me for once contact him if you have any form of hacking problem am sure he will help you THANK YOU.
ReplyDeletecontact: cybergoldenhacker at gmail dot com