Basic Information of The ICE Cyber Crime Center Virus
The ICE Cyber Crime Center attack annoys numerous computer users as a typical ransomware infection. It is a member coming from the infamous Trojan/Win32.Reveton family. Similar as other ransom virus, The ICE Cyber Crime Center infection is a specific malware produced by cyber criminals to make damage on targeted machine and benefit from victims. To get more knowledge about ICE virus, it will typically render a victim’s computer inoperable with the aid of its advanced screen locker techniques, and then demand users to pay a concoctive forfeit in order for the restriction to be removed. Most commonly, the ransom could be $300 or more, which is required to be paid through MoneyPack or other anonymous online payment system. In order to increase its authenticity, this type of ransomware may claim that the computer is being tracked by law enforcement. Without timely fine paid to the authorities, users may encounter further legitimate sanction.
However, the truth is, The ICE Cyber Crime Center has nothing to the with the law enforcement agencies, but is only a hack tool utilized by scammers for money extortion. It is certain that users should ignore the bogus notification displayed by ICE virus, and figure out the effective way to get rid of the threat to avoid worse results. For instance, The ICE Cyber Crime Center may slow down the performance of computer via taking up large amounts of system resources. Meanwhile, this type of ransomware may lead to white screen when an infected computer turns on. The worse thing is, The ICE Cyber Crime Center infection may even open a backdoor for remote hackers with the help of found security vulnerabilities. As a result, not only the affected machine but also user’s privacy will be at high risk out of expectation. So it is urgent to get rid of The ICE Cyber Crime Center virus as long as being informed of its existence to safeguard machine against unexpected damage or loss.
Screenshots of The ICE Cyber Crime Center Virus


How does The ICE Cyber Crime Center Sneak Into PC
1. The ICE Cyber Crime Center virus may be bundled with some malicious applications which seem to be legitimate or helpful for users. When users download and install those applications on computer, The ICE Cyber Crime Center virus could be activated and executed automatically.
2. The ICE Cyber Crime Center virus may be distributed by malicious websites or other legitimate web pages that have been attacked by the malware distributors.
3. The ICE Cyber Crime Center virus may be spread by inserting its malicious codes in some infected email, which contain links or attachments.
4. The ICE Cyber Crime Center virus may be propagated via other Trojan infection, which has the capability to secretly install The ICE Cyber Crime Center virus onto compromised machine.
Auto Removal for The ICE Cyber Crime Center Scam
Many PC users would like to use their trusted antivirus application to safeguard their computer against existed malware or other PC threats. It is evident that a standard antivirus program is capable of detecting and removing various infections from computer. However, The ICE Cyber Crime Center virus is different from common threat, which has the capability to block antivirus from running to avoid auto removal. In this case, auto removal may not be able to handle The ICE Cyber Crime Center virus alone. In this case, you may think over the following manual removal to completely eradicate the virus from computer.
Manual Removal for The ICE Cyber Crime Center Viirus
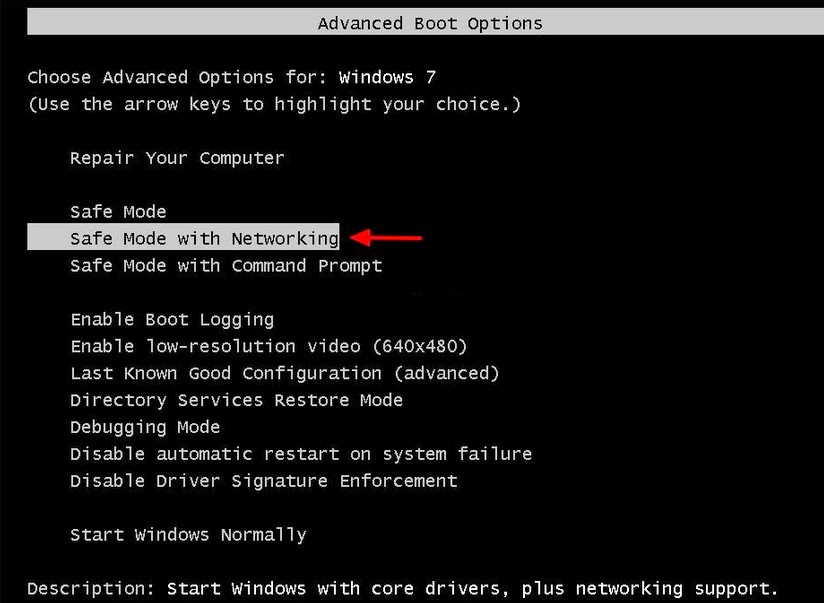
1. Safe Mode with Networking
Reboot the PC and keep pressing F8 key on the keyboard before Windows launches. Hit the arrow keys to choose "Safe Mode with Networking" option, and then tap Enter key to enter Safe Mode with Networking.
2. Show hidden files of The ICE Cyber Crime Center virus.
- Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options. Click the View tab.
- Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
Additional method for Windows 8:
- Log onto Windows 8 computer.
- Click start button on the desktop, click Windows Explorer icon from the taskbar.
- On the opened Libraries window, click View tab.
- Find Option icon and select it.
- In the opened Folder Options window, go to View tab.
- From the Advanced settings list, click to select Show hidden files, folders, and drives radio button under Hidden files and folders category.
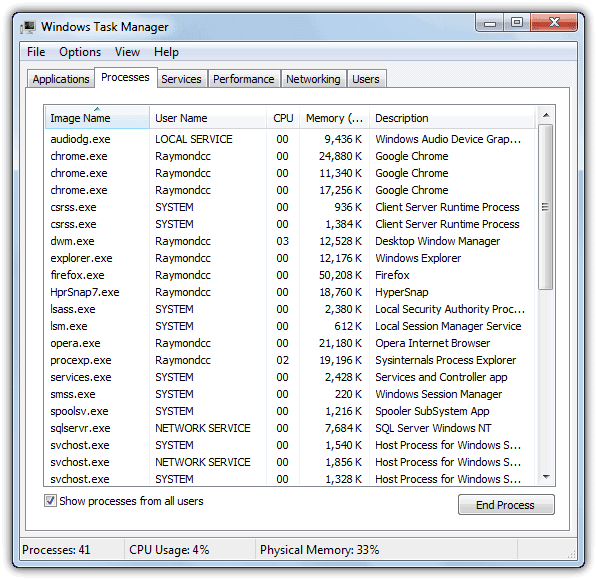
3. Kill the process of The ICE Cyber Crime Center.
4. Remove the files of The ICE Cyber Crime Center.
%AppData%\NPSWF32.dll
%AppData%\Protector-.exe
%AllUsersProfile%\ApplicationData\.exe(rnd)
5. Remove the registry entries of The ICE Cyber Crime Center.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit”={rnd}
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”"
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun”"
Why do I Need to Remove The ICE Cyber Crime Center Scam
- It demands to pay the ransom.
- It encrypts user sensitive documents, multimedia objects or any other files containing important information. Leaves only encrypted data, usually deleting the original files.
- It deletes user documents, multimedia objects or any other files containing important information.
- It corrupts the entire system or installed software by deleting essential system components or important parts of installed software.
- It steals login names, passwords, valuable personal documents, identity data and other user sensitive information.
- It sends all gathered data to a predefined e-mail address, uploads it to a predetermined FTP server or transfers it through a background Internet connection to a remote host.
Pay Attention:
The ICE Cyber Crime Center virus is a dangerous ransomware infection that could bring unexpected damages on targeted computers. It has nothing to do with the authorities, but is only an Internet fraud tool utilized by hackers. PC users are obliged to remove it timely as long as being noticed of its symptoms to avoid worse damage or loss. However, this type of threat is endowed with advanced techniques to block installed antivirus or other security tools from running so that to avoid auto removal. As a result, the almighty manual removal is recommended for users to get rid of all its malicious components. Anyhow, manual removal is a high-level process, which requires certain computer expertise.
If you are not familiar with the manual operation, it is suggested for you to ask help from VilmaTech Certified 24/7 Online Experts for real-time support.


Are you willing to know who your spouse really is, if your spouse is cheating just contact cybergoldenhacker he is good at hacking into cell phones,changing school grades and many more this great hacker has also worked for me and i got results of spouse whats-app messages,call logs, text messages, viber,kik, Facebook, emails. deleted text messages and many more this hacker is very fast cheap and affordable he has never disappointed me for once contact him if you have any form of hacking problem am sure he will help you THANK YOU.
ReplyDeletecontact: cybergoldenhacker at gmail dot com