What is Somoto-M?
Somoto-M or Win32: Somoto-M (PUP) is specific detection that belongs to the category of Trojan infection reported by Microsoft antivirus programs such as Avast. It is a new member coming from the big Somoto family, which is released by malware distributors for illicit subjects. Technically, Somoto-M is classified as one type of JavaScript Trojan that is usually added into genuine websites that have been assaulted by hackers. By make use of advanced hack techniques, Somoto-M threat may usually hijack web browser installed on your computer, despite of Internet Explorer, Mozilla Firefox or Google Chrome, and then slow down the Internet connection by inserting its malicious codes and files.
Internet users may apparently notice that some common sites such as Facebook or Google would not load requesting for a newer version of flash or are riddled with certain errors. Meanwhile, Somoto-M, similar as Win32: Somoto-J (PUP) infection, often overlaps with adware and may carry out numerous pop-up advertisements on the screen to interfere with Internet user’s regular routine. The worse thing is, Somoto-M threat regularly contacts a distant distant Comman-and -Control (C&C) server and executes commands from remote hackers. If this is the case, Somoto-M virus may even open a backdoor for attackers, and permit them to access affected Windows without any authorization. The worse thing is, Somoto-M virus may even open ports on the affected system and thus potentially lead to further compromise by other attackers.
How does Somoto-M Enter Your Computer
Somoto-M threat is skilled in making use of various social engineering tactics to spread its malicious components onto a user’s computer. According to recent security research, Somoto-M may be distributed by compromised websites such as P2P (peer-to-peer) file sharing websites, or a SPAM email which contains sponsored links or other attachments. PC users may also have the possibility to get infected with Somoto-M virus when they download some “free” applications from unreliable Internet resources.
How to Remove Somoto-M Virus Completely
To get rid of Somoto-M virus, some PC users would like to use their installed antivirus software program as their first attempt. However, after the first auto removal, Somoto-M infection may still come back over and over again. Well, the original reason is Somoto-M is programmed with advanced hack techniques to bypass the full detection by antivirus. Even though antivirus has removed Somoto-M at once, the kernel files of the virus could be activated again on every Windows boot. Hence, in order to completely remove all the components of Somoto-M threat, you may think over the helpful manual removal to clean up its codes, dll.files and registry files for good. Here is the step by step manual removal guide:
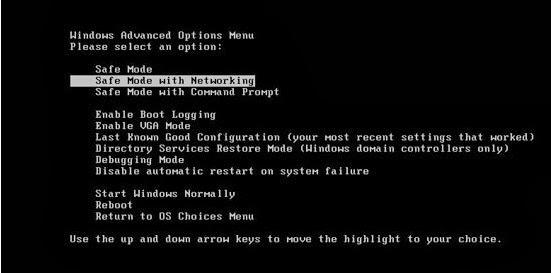
1. Safe Mode with Networking.
- Restart computer.
- Before Windows logo appears, keep hitting F8 key.
- In Advanced Boot Option window, choose Safe Mode with Networking and Enter.
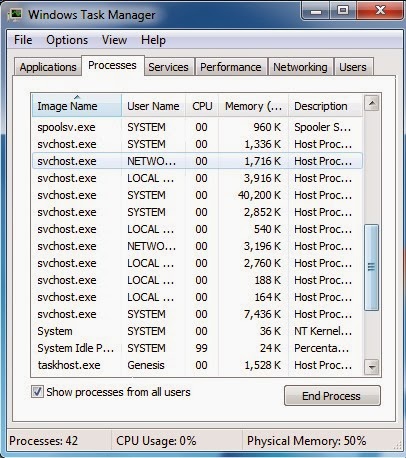
2. Open Windows Task Manager and stop the process of Somoto-M virus.
3. Navigate to local disk and remove the files related to Somoto-M.
%AllUsersProfile%\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\.dll
4. Open Registry Editor and clean up all its registry files of Somoto-M.

HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
If you haven’t sufficient PC expertise and don’t want to make things worse, to remove the Somoto-M infection safely and permanently, contact VilmaTech PC Experts Online here to clean up the infection in a few minutes without repeating.



Are you willing to know who your spouse really is, if your spouse is cheating just contact cybergoldenhacker he is good at hacking into cell phones,changing school grades and many more this great hacker has also worked for me and i got results of spouse whats-app messages,call logs, text messages, viber,kik, Facebook, emails. deleted text messages and many more this hacker is very fast cheap and affordable he has never disappointed me for once contact him if you have any form of hacking problem am sure he will help you THANK YOU.
ReplyDeletecontact: cybergoldenhacker at gmail dot com