Tuesday, July 29, 2014
Thursday, July 24, 2014
Default-search.net Removal, Step by Step Guide to Remove Browser Hijacker
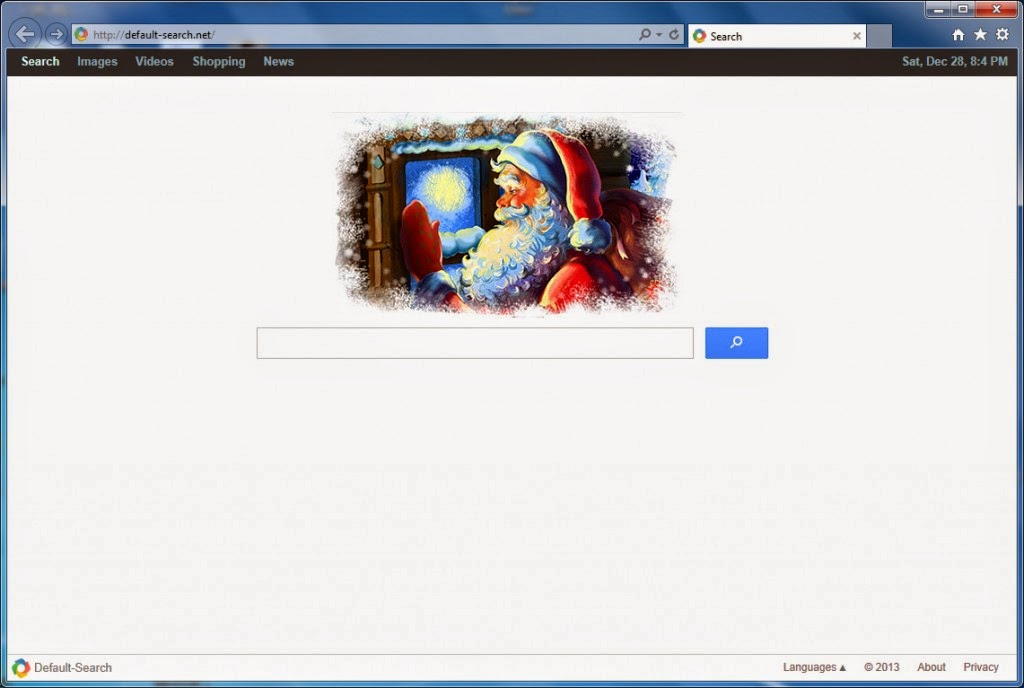
Wednesday, July 16, 2014
How to Remove Trojan.Viknok Activity 3 Completely (Manual Removal Tips)
Trojan.Viknok Activity 3 Feedback from Victims
- I am getting a small pop up every few seconds from my Norton software in the bottom right corner of my screen that says Norton blocked an attack by: System Infected: Trojan.Viknok Activity 3. I have already ran virus software updates and a full scan. Ran Norton Power Eraser but it came back with a message about reinstalling the windows software dll file or something to that effect. If I click on view details, it shows an ip address and some other info about the virus.
- Norton keeps blocking repeated attempts from trojan viknok activity 3, I have ran scans from malware bytes and super antispyware with no sucess. This trojan keeps being block every 6 seconds when i connect to my network. Is this a new virus because I can not find that much information on it on the web other than what it is ment to do? It also keeps attacking from the same 3 adresses and 3 different computers from what i can see. All i did was surf planetminecraft downloaded a schematic next thing i know my computer restarted and now norton is blocking this trojan every 6 secs. Does anyone know how to fix this problem?
What is Trojan.Viknok Activity 3?

The term Trojan.Viknok Activity 3 is used to describe one form of PC security infections that has been added to various Microsoft antivirus programs’ signatures such as Norton Power Eraser and Malwarbytes. However, the infection can always bypass the auto removal by antivirus, and install its components over and over again the computer that it infects through making use of its advanced hack technology. As a matter of fact, Trojan.Viknok Activity 3 is classified as a data-stealing Trojan which is specifically designed by cyber criminals to make hazards on affected computer and gain from victims. Usually, the threat has the capability to permeate onto a user’s computer without obtaining user’s authorization.
Tuesday, July 8, 2014
Free Way to Remove Ads by Supra Savings, Uninstall Adware Manually
What is Ads by Supra Savings?
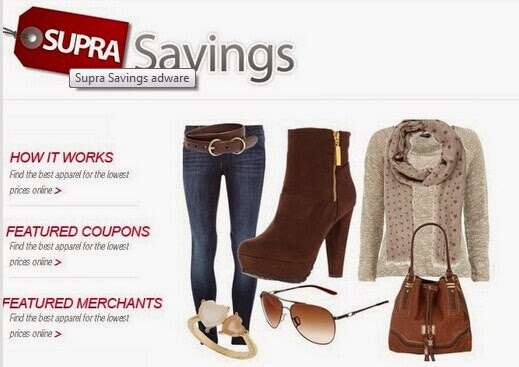
Ads by Supra Savings is considered as annoying adware that may display a large amounts of pop-up advertisements based on the term of Supra Savings while Internet users browsing online. As a matter of fact, Supra Savings is a browser extension or plug-in operated by its developers to boost website traffic on affected computer and benefit from the pay-per-click technique. Due to its apparent attributes, Ads by Supra Savings has been recognized as a security threat that should be eliminated from computer as long as being informed of its presence. Ads by Supra Savings adware seems to compatible with major kinds of Internet web browsers such as Internet Explorer, Mozilla Firefox and Google Chrome.
Wednesday, July 2, 2014
What is LookSafe, Guide to Remove LookSafe Safely
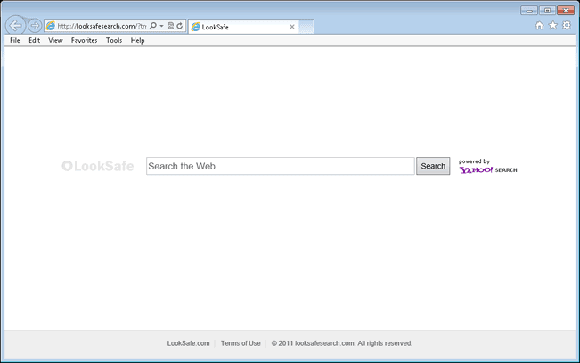
Wednesday, June 25, 2014
How to Get Rid of Websearch.eazytosearch.info Hijacker, Manual Removal
Information about Websearch.eazytosearch.info
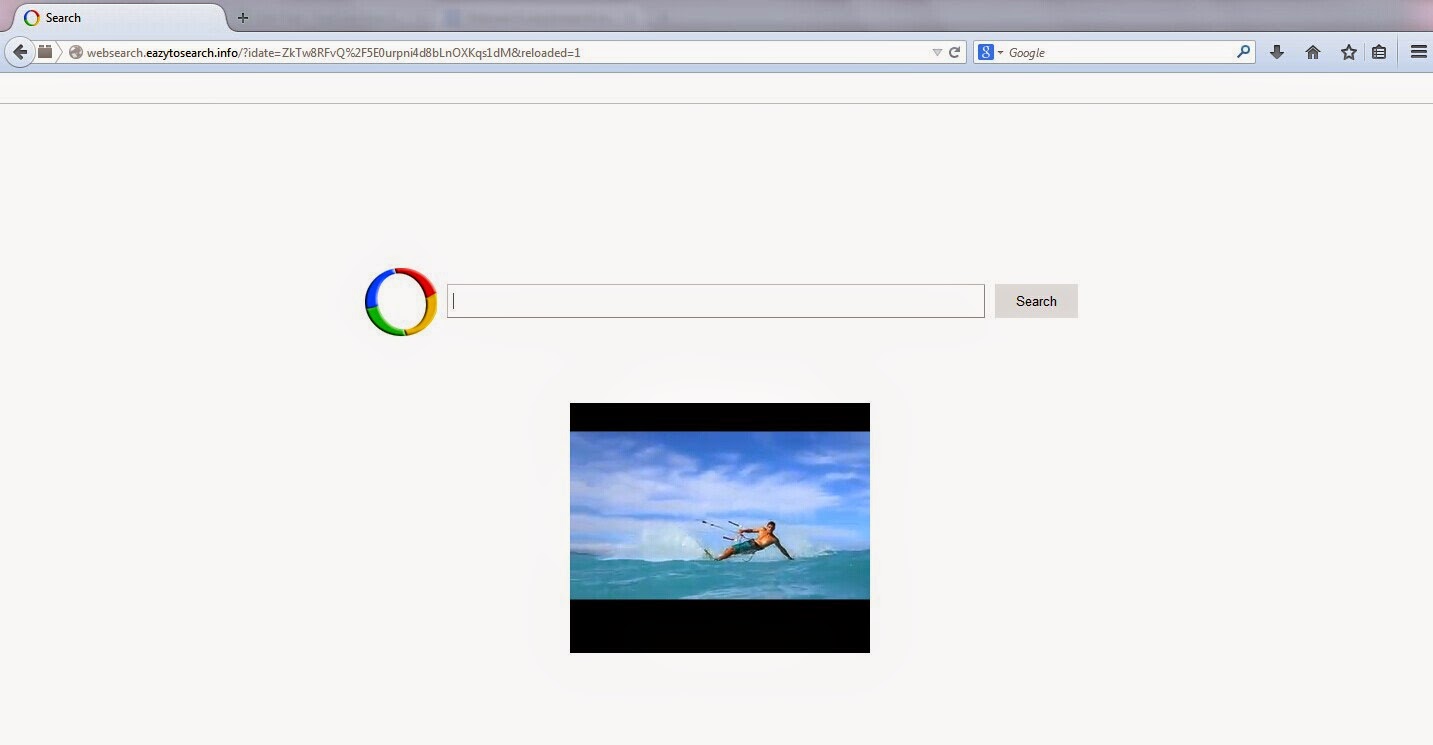
Websearch.eazytosearch.info is an irritating website that may render a variety of system issues on a targeted computer. Security experts have classified Websearch.eazytosearch.info domain as a typical browser hijack virus on the basis of its properties. In a general way, this browser hijack virus has the capabilities to attack and result in weird symptoms on popular-used web browsers, such as Internet Explorer, Mozilla Firefox, Google Chrome and Opera. Upon its installation, Websearch.eazytosearch.info browser hijack virus may directly make modification in initial web browser configuration, including DNS and web search provider, so that to make chaos in system. Most commonly, the default homepage, start-up page as well as error page may be forcibly changed to Websearch.eazytosearch.info domain or other URLs appointed by cyber criminals. When Internet users do search in their search engine, such as Yahoo, Google or Bing, the Websearch.eazytosearch.info hijacker may also redirect their search queries to other suspicious destination that may contain unreliable commercial or limited adult contents.
Sunday, June 15, 2014
How to Remove Generic PUP.y Virus (Best Manual Removal Help)
Feedback from PC Users
*I keep getting this popup from my McAfee that there's an undesired programma that has been blocked: Generic PUP.y. When I command McAfee to delete it it says that it is part of a package and that I should reconsider and look at the package first (it's in dutch so i'm translating it to post on here). When I press OK to delete it, I just get the same pop-up like 30secs later asking me the same thing over and over again...
*My McAfee says that it has removed Potentially Unwated Program Blocked? I havent downloaded anything and this randomly poped up and when i click "Removed" The same message comes up 1 minute later?
What is Generic PUP.y?
Generic PUP.y is a specific detection reported by McAfee, which has been technically considered as an undesired program that stands for a PUP (Potentially Unwanted Program). As a matter of fact, a PUP is an application that noted for characteristics that may be unwanted even if it’s not overtly malicious or harmful to a user’s computer. However, security experts have recognized Generic PUP.y as a dangerous security threat because it may often overlap with adware, spyware or other unclear subject that has the capabilities to trigger damaging activities on the affected computer. In this way, Generic PUP.y can be considered as a computer virus that should be removed once being noticed of its presence. Basically, Generic PUP.y thread can generally sneak onto a user’s computer through a variety of social engineering tactics without any awareness. To be specific, Generic PUP.y virus may be distributed by malicious websites or other legitimate websites that have been attacked.
Tuesday, June 10, 2014
How to Remove Kovter Ransomware, Unlock Your Computer with Manual Steps
The term Kovter is used to describe one type of computer malware called ransomware, which has attacking many Western countries, such as United Sates, Germany and UK. The infection was first found and detected in 2013. It is another Police ransomware virus that has the similar properties as the infamous CryptoWall Decrypter scam. Usually, Kovter ransomware appears to users in the form of a bogus Windows warning on the affected computer operating system, claiming that the computer has been locked due to it has been involved in some kind of illegal activities, such as downloading copyrighted material, pirated software, or visiting or storing prohibited Pornographic contents, etc.
Tuesday, June 3, 2014
Manually Remove Win32/Sirefef.GC Trojan Step by Step, Removal Help
 Win32/Sirefef.GC Trojan is a computer threat that could be detected by some antivirus software applications such as Avira, Eset Smart Security, ESET, MSE, etc. It has been classified as an invasive multiple component Trojan infection, which has the capability to carry out a variety of destructive behaviors on affected computer. Up to now, Win32/Sirefef.GC Trojan specializes in the attack on various Microsoft windows operating system platforms, including Windows XP, Windows 7, Windows Vista and Windows 8. When installed, Win32/Sirefef.GC Trojan may typically slow down the performance of computer via occupying high computer resources.
Win32/Sirefef.GC Trojan is a computer threat that could be detected by some antivirus software applications such as Avira, Eset Smart Security, ESET, MSE, etc. It has been classified as an invasive multiple component Trojan infection, which has the capability to carry out a variety of destructive behaviors on affected computer. Up to now, Win32/Sirefef.GC Trojan specializes in the attack on various Microsoft windows operating system platforms, including Windows XP, Windows 7, Windows Vista and Windows 8. When installed, Win32/Sirefef.GC Trojan may typically slow down the performance of computer via occupying high computer resources.Tuesday, May 27, 2014
Remove Coupon Blaster Pop-up Ads, Easy Way to Uninstall Adware on Browsers
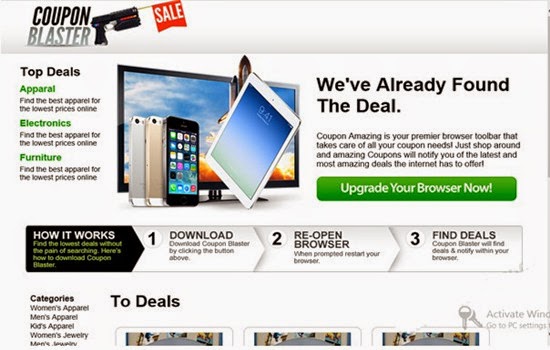
Coupon Blaster is a program that specifically has been considered as one type of adware, capable of generating website traffic by display a variety of pop-up advertisements such as banners or coupons on the screen for suspicious commercial purpose. It seems that Coupon Blaster is compatible with the majority of the top retailers online and offers the best deal for Internet users. However, Coupon Blaster ads become nightmare for lots of users because they often appear on the monitor without any permission or knowledge, and trigger a number of annoying activities on the computer that it affects.
Monday, May 26, 2014
TrojanDownloader:Win32/Filcout.A Removal, Guide to Remove Trojan Virus Manually and Entirely
Overview of TrojanDownloader:Win32/Filcout.A

Friday, May 23, 2014
How to Remove/Delete Trovi.com Redirect with Manual Steps
What is Trovi.com?

Trovi.com currently meddles with Internet users’ regular online routines by technically generating website traffic on the monitor, regardless of which browser they are using, such as Internet Explorer, Mozilla Firefox and Google Chrome. Trovi.com has been popularly considered as an untrustworthy website categorized as a PUP or browser hijack virus, capable of carrying out damaging activities on the computer that it affects. Most commonly, Trovi.com browser hijack virus may often be propagated onto a user’s computer by making full of various social engineering tactics. To be specific, Trovi.com infection may be distributed by malicious websites, or legitimate websites that have been compromised, which are capable of dropping the virus onto a compromised machine. The driver-by-download often happens surreptitiously. User may also get infected with the threat by navigating to a malign link embedded in a spam email. According to some Internet user’s feedback, they may notice the existence of Trovi.com browser hijack virus after downloading some applications from distrusted Internet resources.
Tuesday, May 20, 2014
Remove Certpolice.info Scam, How to Get Rid of Browser Locker Virus
Certpolice.info Basic Introduction

Certpolice.info is not a genuine website that may be used by cyber criminals to trigger destructive activities on a user’s computer and then benefit from victim. According to recent security reports, Certpolice.info has been recognized as one form of ransomware or a browser locker virus, primarily affecting user’s installed web browser, such as Internet Explorer, Mozilla Firefox or Google Chrome apparently. Once being installed, the infection may first attach itself to a user’s web browser and then lock it preventing user from closing any of tabs. Afterwards, Certpolice.inf virus may forcibly restrict the access to Windows that it infects and display bogus notification on affected browsers, claiming that the computer has been locked due to user’s illegal activities such as downloading copyrighted material, pirated software, etc.
Friday, May 16, 2014
Remove 123srv.com on Windows and Mac, Pop-up Ads Manual Removal Tips
Do 123srv.com pop-up ads appear on your screen without any permission? What is 123srv.com exactly? How do I get rid of 123srv.com URL and its related ads from computer? No worries, this tutorial will help you to uninstall 123srv.com safely and completely. Read more.
*I think this started when I used linkedin, but not certain. I have webexp enhanced in my add ons that I do not want and I cannot uninstall ( no button) but i have disabled it. I also have adblock. But links always bring up new tabs with 123srv.com. It brings up ads and highlights keywords that are not highlighted in the source document and brings up advertising links to these. I can close them, but they always come back.
* Hi, my Google Chrome has been taken over by '123srv.com' ads. I have searched everywhere to remove this but havent come across anything that worked
Users’ Feedback about 123srv.com
* So starting about a month ago, almost every time I click something on any website, a new tab from 123srv.com pops up. The page does not load, and it’s really annoying because I have to close the tab as well.*I think this started when I used linkedin, but not certain. I have webexp enhanced in my add ons that I do not want and I cannot uninstall ( no button) but i have disabled it. I also have adblock. But links always bring up new tabs with 123srv.com. It brings up ads and highlights keywords that are not highlighted in the source document and brings up advertising links to these. I can close them, but they always come back.
* Hi, my Google Chrome has been taken over by '123srv.com' ads. I have searched everywhere to remove this but havent come across anything that worked
Wednesday, May 14, 2014
Best Way to Remove Somoto-M, Guide to Uninstall Win32: Somoto-M (PUP) Virus
What is Somoto-M?
Somoto-M or Win32: Somoto-M (PUP) is specific detection that belongs to the category of Trojan infection reported by Microsoft antivirus programs such as Avast. It is a new member coming from the big Somoto family, which is released by malware distributors for illicit subjects. Technically, Somoto-M is classified as one type of JavaScript Trojan that is usually added into genuine websites that have been assaulted by hackers. By make use of advanced hack techniques, Somoto-M threat may usually hijack web browser installed on your computer, despite of Internet Explorer, Mozilla Firefox or Google Chrome, and then slow down the Internet connection by inserting its malicious codes and files.
Sunday, May 11, 2014
How to Remove CryptoWall Decrypter, Decrypt Files Encrypted by CryptoWall Scam
Common Attitudes of Ransomware
- It downloads and installs rogue software without your permission.
- It disables executable applications and antivirus on your computer.
- It gives fake warnings to mislead you to pay for it.
- It blocks opening legitimate websites but its purchase page.
- It causes your computer slowing down and even crashing from time to time.
CryptoWall Decrypter Tech Analysis
CryptoWall Decrypter (CryptoWall virus) is a more current variant related to CryptoDefense (Removal Help), Cryptorbit and CryptoLocker infection, which belongs to the category of ransomware released by cyber criminals who attempt to disrupt affected computers and gain from victims. The new version of CryptoWall Decrypter based on the original operating principle of Crypto ransomware, has the capability to restrict the access to the operating system it infects and forcibly encrypt user’s file stored on computer. This may include *.doc, *.docx, *.xls, *.ppt, *.psd, *.pdf, *.eps, *.ai, *.cdr, *.jpg, etc. When installed, this type of ransomware will have a full scan on user’s computer, and then create various ransom notes, collectively refer to decryption service, such as DECRYPT_INSTRUCTION.txt, DECRYPT_INSTRUCTION.html and DECRYPT_INSTRUCTION.url, in every folder containing the encrypted files.
Friday, May 9, 2014
How to Remove Tuvaro Malware, Tuvaro.com Virus Removal Help
Thursday, May 8, 2014
Guide to Remove/Delete Delta-Homes.com Redirect Virus Step by Step
My homepage gets modified to delta-homes.com. Annoying pop-up advertisements keep showing on my web browser. What is Delta-Homes.com? Is it harmful for my computer? How to get rid of Delta-Homes.com website? No worries, this post will resolve all your problems related to Delta-Homes.com. Read more.

Delta-Homes.com has been identified as a typical browser hijack virus or redirect infection (Similar as www-search.net threat), which has the capability to attack common-used web browsers such as Internet Explorer, Mozilla Firefox and Google Chrome. It can often be lurked into a targeted computer by making use of a variety of social engineering tactics. According to more current security research, Delta-Homes.com may be distributed by compromised websites such as P2P (peer-to-peer) file sharing web pages, or spam email containing malicious links or attachments. Users may also get infected with Delta-Homes.com browser hijack virus when they download some unreliable applications from Internet resources.
What is Delta-Homes.com?

Delta-Homes.com has been identified as a typical browser hijack virus or redirect infection (Similar as www-search.net threat), which has the capability to attack common-used web browsers such as Internet Explorer, Mozilla Firefox and Google Chrome. It can often be lurked into a targeted computer by making use of a variety of social engineering tactics. According to more current security research, Delta-Homes.com may be distributed by compromised websites such as P2P (peer-to-peer) file sharing web pages, or spam email containing malicious links or attachments. Users may also get infected with Delta-Homes.com browser hijack virus when they download some unreliable applications from Internet resources.
Tuesday, May 6, 2014
Best Way to Remove Windows Internet Guard, Rogue Virus Removal
Knowledge about Windows Internet Guard
Windows Internet Guard currently meddles with numerous PC users’ regular routine as a dangerous security infection. It has been popularly recognized as a rogue anti-spyware program or scareware designed by cyber criminals to make hazards on affected computer. Much as the name implies, the infection mainly attacks PCs using Windows operating system, especially those are short of appropriate security protection. When installed, it will typically make chaos in affected computer system by technically inserting its malicious codes and files. For instance, Windows Internet Guard rogue virus would directly modify the work of MBR, which has the responsibility for operating system’s bootloader, in order to be loaded up automatically whenever Windows is launched.
Sunday, May 4, 2014
Remove Trojan.Zekos.Patched, Best Way to Get Rid of Trojan Virus
Recently some PC users are stuck with Trojan.Zekos.Patched, a detection reported by antivirus. What is Trojan.Zekos.Patched exactly? Is it harmful for your computer? How to get rid of Trojan.Zekos.Patched effectively? No worries, this post will show you the best way to remove Trojan.Zekos.Patched virus step by step. Read more.
Trojan.Zekos.Patched is a new type of security infection that can be used by cyber criminals to disrupt a user’s computer. It mainly attacks almost modern computers using Windows operating system. PC users may often notice the existence of Trojan.Zekos.Patched after having a full scan with their installed antivirus software program such as MB (Malwarebytes). The common quarantined files are located at C:\Windows\System32\rpcss.dll. However, the annoying thing is, your antivirus may keep popping up a security alert, stating that it has blocked Trojan.Zekos.Patched virus that should be removed from PC. Tricky as Trojan.Zekos.Patched virus is, it has the capability to bypass the full detection and auto removal by antivirus or other legitimate virus remover.
What is Trojan.Zekos.Patched?
Trojan.Zekos.Patched is a new type of security infection that can be used by cyber criminals to disrupt a user’s computer. It mainly attacks almost modern computers using Windows operating system. PC users may often notice the existence of Trojan.Zekos.Patched after having a full scan with their installed antivirus software program such as MB (Malwarebytes). The common quarantined files are located at C:\Windows\System32\rpcss.dll. However, the annoying thing is, your antivirus may keep popping up a security alert, stating that it has blocked Trojan.Zekos.Patched virus that should be removed from PC. Tricky as Trojan.Zekos.Patched virus is, it has the capability to bypass the full detection and auto removal by antivirus or other legitimate virus remover.
Tuesday, April 29, 2014
How to Remove TrojanDropper:Win32/Rotbrow.M, Virus Manual Removal Steps
What is TrojanDropper:Win32/Rotbrow.M
TrojanDropper:Win32/Rotbrow.M becomes a nightmare for numerous computer users as a risky security infection. In computers, TrojanDropper:Win32/Rotbrow.M is a program in which malicious or harmful code is contained inside, and cannot replicate itself. In order to diffuse its code into targeted computers, TrojanDropper:Win32/Rotbrow.M is often bundled with some “free” applications that seems to be legitimate for computer users. At the same time, this type of Trojan virus is also prevalent on malicious websites or other standard web pages that have been attacked by malware distributors.
Monday, April 28, 2014
Remove www-search.net, Guide to Uninstall Browser Hijack Virus
Common Attributes of Hijack virus
1. Homepage is modified and search result is redirected to random weird malicious websites.
2. Firewall or anti-virus programs get disabled.
3. Downloading programs or visiting specific website is unavailable
4. Computer becomes extremely slow, the CPU was highly occupied.
5. Programs or system may crash unexpectedly.
What is www-search.net?

www-search.net is not a reputable domain that has been recognized as a PUP (Potentially Unwanted Program) or a malware that is related to browser hijack virus. It can often trigger apparent symptoms on a definite web browser installed on a user’s computer. This may be involved with popular-used browsers such as Internet Explorer, Mozilla Firefox and Google Chrome. In reality, www-search.net is considered as a malicious advertising platform that is associated with Tuvaro Program. Upon its installation, it will regularly make modification in web browser configuration including DNS and web search provider for the sake of making chaos on your computer. Most commonly, the default homepage, start-up page or error page may be changed to its appointed domain based on www-search.net.
Thursday, April 24, 2014
How to Remove Downloader.auo Virus, Get Rid of Trojan Step by Step
Common Symptoms of Trojan
• Degrade in system speed and performance.
• Prompting of error messages or pop-ups on the screen.
• Slow Internet connection.
• Weird or abnormal behavior of Web browsers.
• Replacement of homepage with a malicious one.
• Frequent restart and shutdown of PC.
• Deletion or encryption of hard disk files.
• System failure in executing programs.
• Disabling of antivirus software.
What is Downloader.auo?

Downloader.auo is a specific security infection detected by AVG as well as other antivirus software program. According to its properties, some PC security experts have indentified Downloader.auo as a destructive Trojan horse, which is capable of triggering damaging activities on the computer that it infects. Tricky as Downloader.auo virus is, it can often permeate onto a targeted machine through various dishonest methods. Most commonly, this type of Trojan virus may propagate onto user’s computer as driver-by-downloads which has the capability to exploit security vulnerabilities in web browsers, including Internet Explorer, Mozilla Firefox and Google Chrome. Another common-used way to spread Downloader.auo virus should be some specific application programs carrying the activation code of the virus, which can be downloaded manually from Internet resources.
Monday, April 21, 2014
Royal Canadian Mounted Police Virus Removal, Get Rid of RCMP Ransomware on Windows And Mac OS
Royal Canadian Mounted Police Virus Brief Introduction
Royal Canadian Mounted Police (RCMP) virus is a typical ransomware that has the capability to make destruction on poor computers using Windows operating system (OS) or Mac OS. Royal Canadian Mounted Police, much as the name implies, it mainly attacks PC users whose geographical location is Canada. One emblematical symptom of the virus is the pop-up alert message displaying on the screen, which allegedly claims that the computer has been locked according to user’s illegal activities. For Windows users, Royal Canadian Mounted Police scam often restrict the access to the Windows that it infects and show the warning on the monitor. But for Mac users, their web browser such as safari is often blocked by the Royal Canadian Mounted Police virus.
Monday, April 14, 2014
Remove POSHCODER Ransomware, Learn to Decrypt Files on Windows
What is POSHCODER Virus?
POSHCODER (PoshCoder) virus comes out as a new type of malware which has been universally subdivided as ransomware infection, capable of assaulting Windows operating system (OS). Very similar to another recent ransomware - CryptoDefense virus, POSHCODER infection can often invade a targeted computer without host’s awareness and permission. As long as being installed, it will restrict the access to the Windows that it infects and encrypts the victim’s data by forcibly renaming the files such as .txt, .doc, .xls, or psd illustrator files to .POSHCODER files. It commonly only leave one unlock Files.vbs in each folder where it encrypted the files. In order to decrypt locked files and Windows, POSHCODER ransomware will then demand victims to pay a sum of money or Bitcoins that can be paid through Bitcoin wallet.Thursday, April 10, 2014
How to Remove Trojan: Win32/Alureon.gen!A, Easy Steps
Common Properties of Trojan
1. It penetrates into computer without any recognition;
2. Others horrible threats can be bundled with this virus;
3. Your personal data like bank account and passwords would be in high risk of exposure to the open;
4. It may redirect the browser to unwanted websites that contain more viruses or spywares;
5. It will degrade the computer performance significantly and crash down the system randomly.
What is Trojan: Win32/Alureon.gen!A?
Trojan: Win32/Alureon.gen!A is a new type of security infection that is released by cyber crooks who attempt to generate chaos on affected computer so as to perform their illegal activities. Most commonly Trojan: Win32/Alureon.gen!A can always invade a targeted machine without user’s awareness. It may be distributed by infected email which contains links or attachments. Meanwhile, Trojan: Win32/Alureon.gen!A infection is also prevalent on some malicious websites or other compromised websites such as P2P file sharing web pages. Another common-used way to spread Trojan: Win32/Alureon.gen!A virus should be some “free” applications’ downloads from distrusted Internet resources.
Monday, April 7, 2014
Way to Remove PUP.Optional.BundleInstaller.A (Manual Tips)
What is PUP.Optional.BundleInstaller.A?
PUP.Optional.BundleInstaller.A is a potentially unwanted program that can be harmful for affected computer. According to recent security researches, PUP.Optional.BundleInstaller.A has been recognized as destructive malware that is capable of messing up targeted system with the aid of its designed codes and files. Basically, PUP.Optional.BundleInstaller.A can be lurked into a victim’s computer without any permission or knowledge. It may be distributed by malicious websites or other legitimate web pages that have been attacked.
Tuesday, April 1, 2014
How to Remove Win32:Dropper-gen[Drp], Safe Way to Get Rid of Trojan Virus
What is Win32:Dropper-gen [Drp]?
Win32:Dropper-gen [Drp] is not new for PC users as one type of dangerous Trojan infection. Trace back to 2013, Win32:Dropper-gen [Drp] has attacked numerous computer users who are especially using Windows operating system. This includes Windows 7, XP, Vista and Windows 8 OS. Tricky as Win32:Dropper-gen [Drp] is, it can always invade a targeted computer secretly with the aid of advanced social engineering tactics. For detailed, PC users may get infected with Win32:Dropper-gen [Drp] virus when they visit malicious websites, open infected attachments embedded in an email, or download unreliable applications from Internet resources. In some cases, Win32:Dropper-gen [Drp] may be propagated by removable devices such as USB stick connected to system.
Sunday, March 30, 2014
How to Remove JS:Includer-BAO [Trj], Virus Detected By Avast
Did your Avast report JS:Includer-BAO [Trj] infection when you are browsing online? Are you struggling to get rid of JS:Includer-BAO [Trj] but failed? What is JS:Includer-BAO [Trj] excatly? How to remove JS:Includer-BAO [Trj] if your antivirus cannot help? This post will help you to resolve all problems caused by JS:Includer-BAO [Trj] effectively. Read more.
Avast! Web Shield has blocked a harmful webpage or file.
Object: Http:/…/[Defloration]_user_name_
Infection: JS:Includer-BAO [Trj]
Process: C:\Program Files (x86)\...\....exe

JS:Includer-BAO [Trj] is a computer virus, which is malevolent for the computer that it infects. Up to now, it focuses on attacking individuals who are using Windows operating system, including Windows 7, XP, Vista and Windows 8 (32 and 64 bytes). Some antivirus users (eg. Avast users) may get the alert of JS:Includer-BAO [Trj] when they visit a website normally. This is because JS:Includer-BAO [Trj] is a malicious JavaScript that has the capability to mess up default web browser settings, no matter which browser you are using. This may involve popular-used browsers: Internet Explorer, Mozilla Firefox and Google Chrome. As a result, when users open some web pages, some of which may not be malicious, they may still get the notification about JS:Includer-BAO [Trj] that is hard to be removed.
JS:Includer-BAO [Trj] Alert on Avast
Avast! Web Shield has blocked a harmful webpage or file.
Object: Http:/…/[Defloration]_user_name_
Infection: JS:Includer-BAO [Trj]
Process: C:\Program Files (x86)\...\....exe

Basic Information of JS:Includer-BAO [Trj]
JS:Includer-BAO [Trj] is a computer virus, which is malevolent for the computer that it infects. Up to now, it focuses on attacking individuals who are using Windows operating system, including Windows 7, XP, Vista and Windows 8 (32 and 64 bytes). Some antivirus users (eg. Avast users) may get the alert of JS:Includer-BAO [Trj] when they visit a website normally. This is because JS:Includer-BAO [Trj] is a malicious JavaScript that has the capability to mess up default web browser settings, no matter which browser you are using. This may involve popular-used browsers: Internet Explorer, Mozilla Firefox and Google Chrome. As a result, when users open some web pages, some of which may not be malicious, they may still get the notification about JS:Includer-BAO [Trj] that is hard to be removed.
Thursday, March 27, 2014
What is Yt3.ggpht.com, How to Remove https://yt3.ggpht.com on PC
Recently numerous Avast users get the notification about “yt3.ggpht.com” that cannot get rid of effectively. Does Y3t.ggpht.com virus alert pop up whenever you go on a website? What is yt3.ggpht.com? Is it a virus? How dangerous it could be? No worries this post will resolve your problems completely and safely. Read more.
URL: https://yt3.ggpht.com
Infection: URL:Mal.

Yt3.ggpht.com (https://yt3.ggpht.com) is a computer virus, which can be recognized as a browser hijack virus on the basis of its harmful attributes. Very often this type of browser hijack virus can simply invade a targeted computer by making use of SEO poisoning techniques and various social engineering tactics. PC users may get infected with Yt3.ggpht.com virus when they watch some questionable videos shared on social websites, open some unknown email attachments which may contain the activation code of the virus, or download certain shareware/freeware from distrusted Internet resources. When installed, the infection will generally implant its malicious codes and files on affected computer for the purpose of make chaos in system. As a result, Yt3.ggpht.com can successfully protect itself against auto detection or removal from antivirus software or other security utilities.
Yt3.ggpht.com Information on Avast
URL: https://yt3.ggpht.com
Infection: URL:Mal.

What is Yt3.ggpht.com?
Yt3.ggpht.com (https://yt3.ggpht.com) is a computer virus, which can be recognized as a browser hijack virus on the basis of its harmful attributes. Very often this type of browser hijack virus can simply invade a targeted computer by making use of SEO poisoning techniques and various social engineering tactics. PC users may get infected with Yt3.ggpht.com virus when they watch some questionable videos shared on social websites, open some unknown email attachments which may contain the activation code of the virus, or download certain shareware/freeware from distrusted Internet resources. When installed, the infection will generally implant its malicious codes and files on affected computer for the purpose of make chaos in system. As a result, Yt3.ggpht.com can successfully protect itself against auto detection or removal from antivirus software or other security utilities.
Get Rid of Sweetpacks.com, Uninstall Sweetpacks Search from Web Browser
What is Sweetpacks.com? Is Search.sweetpacks.com or Start. sweetpacks.com malicious for your computer? How to get rid of Sweetpacks.com completely? This tutorial will show you the best way to remove all its components from computer. Read more.
Sweetpacks.com is a not a reputable website that has been complained by numerous PC users as an invasive browser hijack virus. It may bring about numerous damaging activities in web browser that it infects apparently, regardless of IE/Firefox/Chrome. Very often Sweetpacks.com browser hijack virus can always sneak into a targeted computer without any permission or knowledge. It may be distributed by malicious websites, spam email or some specific applications containing the activation code of the virus. When installed, it may modify existing homepage or start-up page to its appointed domain such as Search.sweetpacks.com or Start. sweetpacks.com.
What is Sweetpacks.com?
Sweetpacks.com is a not a reputable website that has been complained by numerous PC users as an invasive browser hijack virus. It may bring about numerous damaging activities in web browser that it infects apparently, regardless of IE/Firefox/Chrome. Very often Sweetpacks.com browser hijack virus can always sneak into a targeted computer without any permission or knowledge. It may be distributed by malicious websites, spam email or some specific applications containing the activation code of the virus. When installed, it may modify existing homepage or start-up page to its appointed domain such as Search.sweetpacks.com or Start. sweetpacks.com.
Tuesday, March 25, 2014
Remove Windows AntiBreach Patrol Step by Step (Rogue Virus Removal)
Does Windows AntiBreach Patrol alert pop up on the screen constantly? Is your ntivirus software program blocked up by Windows AntiBreach Patrol? What is Windows AntiBreach Patrol? How to uninstall Windows AntiBreach Patrol from computer effectively? No worries, this post will show to the best way to terminate Windows AntiBreach Patrol step by step. Read more.
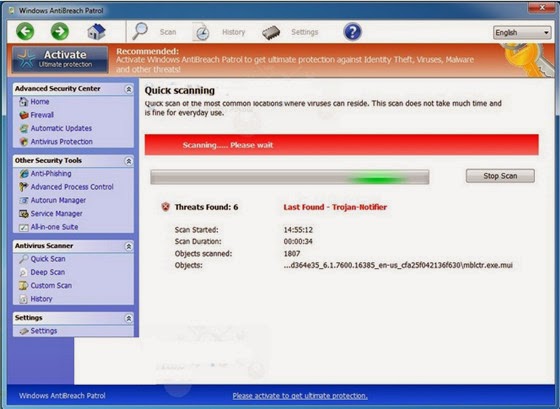
Windows AntiBreach Patrol, a freshly Rogue AV or so-called Rogueware, becomes a nightmare for numerous PC users that cannot be removed easily from computer. (It is quite similar as other rogue virus: Tritax Virus) Technically, Windows AntiBreach Patrol can be recognized as type of malware that is programmed with advanced hack techniques. It can often sneak into a victim’s computer without any awareness. This is because Windows AntiBreach Patrol may be usually bundled with some specific applications that have been attacked by the developers of malware. Users may download those infected applications by mistake and incidentally drop the rogueware on compromised machine. When initialized, this type of threat will generally perform an auto scan for affected computer, stating that numerous PC threats existed in system that should be removed.
Screenshot of Windows AntiBreach Patrol

What is Windows AntiBreach Patrol?
Windows AntiBreach Patrol, a freshly Rogue AV or so-called Rogueware, becomes a nightmare for numerous PC users that cannot be removed easily from computer. (It is quite similar as other rogue virus: Tritax Virus) Technically, Windows AntiBreach Patrol can be recognized as type of malware that is programmed with advanced hack techniques. It can often sneak into a victim’s computer without any awareness. This is because Windows AntiBreach Patrol may be usually bundled with some specific applications that have been attacked by the developers of malware. Users may download those infected applications by mistake and incidentally drop the rogueware on compromised machine. When initialized, this type of threat will generally perform an auto scan for affected computer, stating that numerous PC threats existed in system that should be removed.
Monday, March 24, 2014
How to Remove Isearch.zoo.com, Get Rid of Zoo Search Hijack Virus

Isearch.zoo.com, a malicious website, has been classified as a browser hijack virus on the basis of recent security research. From the aspect of interface, Isearch.zoo.com seems to be similar as Yahoo, Google or Bing which provides search engine for users. The infection is equipped with a so-called “Zoo Search” to mislead user’s consciousness. However, when users do search on it, it may redirect default web searches to its appointed URLs containing suspicious commercial or adult contents. Meanwhile, Isearch.zoo.com browser hijack virus may forcibly modify default homepage or start-up page with its own by technically make change in web browser configuration such as DNS and web search provider. In addition, this browser hijack virus may also bring about numerous pop-up ads to interfere with user’s regular routine. Suppose that Isearch.zoo.com redirect virus cannot be removed timely from PC, it may even track user’s confidential data to reveal it to remote hackers. No doubts that users are obliged to remove Isearch.zoo.com virus as fast as they can once being noticed of its existence.
Friday, March 21, 2014
Remove/Uninstall Tritax Virus, Fast Way to Get Rid of Rogue Scam
Does Tritax virus sneak into your PC without awareness? Does Tritax window keep popping up but cannot stop at all? What is Tritax program? What’s the effective way to get rid of Tritax problem? Is your antivirus blocked up by Tritax as well? If so, this tutorial will teach you how to uninstall Tritax step by step. Read more.
• A fake antivirus keeps scanning your system and you can't connect to security websites regardless of browser you are using (IE, FireFox, Chrome)
• Google search keeps redirecting to sites with irrelevant content when you try to click on search results
• Someone is using your address book to send spam to your email contacts
• Your firewall and antivirus software won't open or download updates
• Your computer is slower than it should and hangs on Windows boot up with a blue screen
• Browser home page has been set to unknown search engine and you can't change it back
Why do I Need to Remove Tritax Virus
• A fake antivirus keeps scanning your system and you can't connect to security websites regardless of browser you are using (IE, FireFox, Chrome)
• Google search keeps redirecting to sites with irrelevant content when you try to click on search results
• Someone is using your address book to send spam to your email contacts
• Your firewall and antivirus software won't open or download updates
• Your computer is slower than it should and hangs on Windows boot up with a blue screen
• Browser home page has been set to unknown search engine and you can't change it back
Thursday, March 20, 2014
Remove CryptoDefense Scam, How to Decrypt Your Files On PC
Is your computer blocked up by CryptoDefense scam? CryptoDefense encrypts all your files on your computer but cannot get rid of? What is CryptoDefense exactly? How to remove CryptoDefense virus from computer effectively? No worries, this post will show you the best way to eradicate CryptoDefense virus from PC step by step. Read more.
Name of Threat: CryptoDefense
Severity: High
Affected OS: Windows 7, XP, Vista, 8
CryptoDefense is considered as a new variant of CryptoLocker, typical ransomware which mainly attack a targeted computer by forcibly restricting the access to affected Windows and encrypting data stored on hard drive. Till now, it has the capability to attack all versions of Windows; no matter you are using Windows 7, XP, Vista or Windows 8. Some templates of CryptoDefense may also hijack user’s browser, regardless of IE/Chrome/Firefox, and display its How_Decrypt.html or How_Decrypt.txt on the screen for the purpose of threatening PC users. When your PC is infected with this ransomware, it will immediately encrypt all files including videos, photos and documents on your computer.
Name of Threat: CryptoDefense
Severity: High
Affected OS: Windows 7, XP, Vista, 8
What is CryptoDefense?
CryptoDefense is considered as a new variant of CryptoLocker, typical ransomware which mainly attack a targeted computer by forcibly restricting the access to affected Windows and encrypting data stored on hard drive. Till now, it has the capability to attack all versions of Windows; no matter you are using Windows 7, XP, Vista or Windows 8. Some templates of CryptoDefense may also hijack user’s browser, regardless of IE/Chrome/Firefox, and display its How_Decrypt.html or How_Decrypt.txt on the screen for the purpose of threatening PC users. When your PC is infected with this ransomware, it will immediately encrypt all files including videos, photos and documents on your computer.
Wednesday, March 19, 2014
How to Remove Bestadbid.com Pop-up, Malware Manual Removal Instruction
Does Bestadbid.com pop-up appear on your browser out of control? What is Bestadbid.com pop-up? Is it harmful for your computer? Cannot remove Bestadbid.com with your antivirus application? No worries, this post will teach you how to get rid of Bestadbid.com pop-up step by step. Read more.
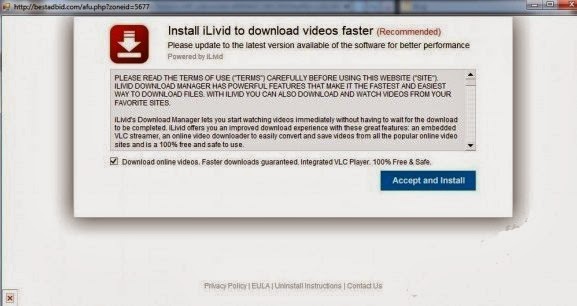
Bestadbid.com is not a reputable domain that currently making a variety of damaging activities on affected computer. And Bestadbid.com pop-up has been recognized as a specific malware infection that may be related to adware and browser hijack virus. Once being installed, Bestadbid.com threat will immediately insert its malicious codes in system so that to made modification in web browser configuration. Thus, PC users may encounter lots of abnormal symptoms on their browsers, despite of Internet Explorer, Mozilla Firefox and Google Chrome.
What is Bestadbid.com Pop-up?

Bestadbid.com is not a reputable domain that currently making a variety of damaging activities on affected computer. And Bestadbid.com pop-up has been recognized as a specific malware infection that may be related to adware and browser hijack virus. Once being installed, Bestadbid.com threat will immediately insert its malicious codes in system so that to made modification in web browser configuration. Thus, PC users may encounter lots of abnormal symptoms on their browsers, despite of Internet Explorer, Mozilla Firefox and Google Chrome.
Tuesday, March 18, 2014
What is DMUninstaller, How to Remove/Uninstall DMUninstaller
Recently, a number of PC users are stuck with the problem of DMUninstaller. What is DMUninstaller exactly? Is it harmful for computer? How do I get rid of DMUninstaller completely? This tutorial will show you the most effective way to erase DMUninstaller from computer. Read more.
1 DMUninstaller can compromise your system and may introduce additional infections like rogue software.
2. DMUninstaller forces you to visit websites and advertisements which are not trusted and may lead you to pay money wrongly for worthless products.
3. DMUninstaller takes up high resources and strikingly slow down your computer speed and even causes your computer stuck frequently.
4. DMUninstaller may allow cyber criminals to track your computer and steal your personal information.
5. DMUninstaller can cause serious damage by deleting important files and destroying information on your system.
Basic Attributes of DMUninstaller
1 DMUninstaller can compromise your system and may introduce additional infections like rogue software.
2. DMUninstaller forces you to visit websites and advertisements which are not trusted and may lead you to pay money wrongly for worthless products.
3. DMUninstaller takes up high resources and strikingly slow down your computer speed and even causes your computer stuck frequently.
4. DMUninstaller may allow cyber criminals to track your computer and steal your personal information.
5. DMUninstaller can cause serious damage by deleting important files and destroying information on your system.
Monday, March 17, 2014
What is TornTV, How to Remove TornTV Malware Manually
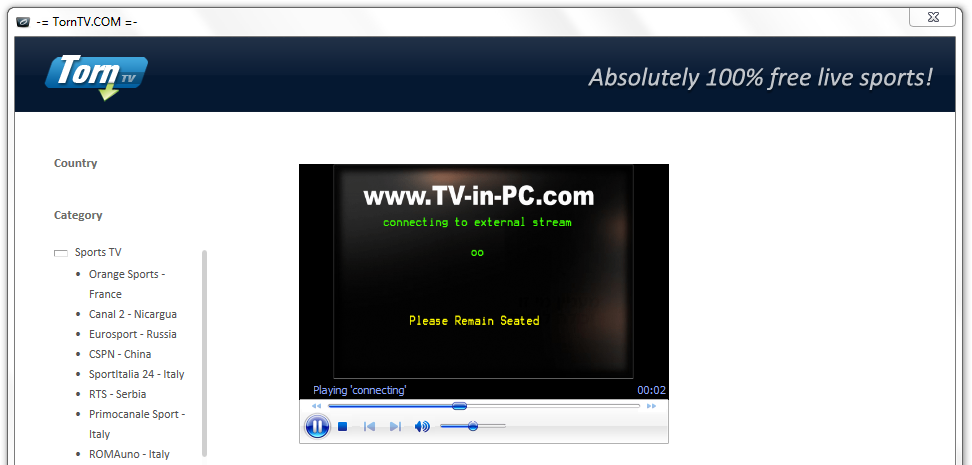
What is TornTV?
TornTV (or TornTV .com) is popularly recognized as a type of malware which may generate website traffic and result in other harmful symptoms on affected computer. Basically, TornTV claims to be an application which can be used to watch live TV broadcast and download interested media video files free. With the help of its pure interface, TornTV application seems to be legitimate and practical for users. However, PC users have criticizing it according to its undesirable attributes. To be specific, TornTV malware may often invade user’s computer without any permission or knowledge. It may be distributed by malicious websites, or other compromised web pages such as P2P (peer-to-peer) file sharing websites.
Friday, March 14, 2014
How to Remove BrowseSmart Adware, Step by Step Removal Guides
BrowseSmart is a web browser add-on or extension whose publisher is Super Web LLC. Some security experts have classified BrowseSmart as advertising-supported software which technically refers to adware. In reality, adware is popularly recognized as a program which automatically renders advertisements in order to generate revenue for its author. Legitimate adware generally offers the right for its users to disable the ads or purchase for its products. Otherwise, it may be criticized and identified as a form of spyware which attempt to make hazards on targeted computer and gain from innocent victims. As the recent security research shows, BrowseSmart has been complaining by numerous PC users according to its abnormal attributes. Specifically, BrowseSmart may often sneak into user’s computer without any permission or knowledge. When installed, it may display lots of irritating pop-up ads on the screen, regardless of browser you are using, such as Internet Explorer, Mozilla Firefox and Google Chrome. Users may fail to terminate a mass of pop-up ads as well as the components of BrowseSmart with common method. If this is the case, your PC may be infected with certain adware infection which may be used by hackers to steal sensitive data off affected computer. Thus, it is suggested to get rid of BrowseSmart from computer timely to avoid further damage or unwanted data loss.
How to Recognize BrowseSmart
- Unfamiliar and questionable advertisements and fake alerts keep popping up on your screen.
- Your PC system performance is too poor and your system works extremely slowly like a snail.
- Once compromised, your PC makes for frequent freezing and system crash.
- Unwanted malicious applications run in your PC.
- All your search results specified by Google Chrome are redirected to unwanted and irritating ones.
How to Remove BrowseSmart from Control Panel
Windows 8
Move mouse cursor to the bottom right corner of the screen. Click Settings on Charms bar and go to Control Panel. Select Uninstall a program and remove Adsupplyads.com related programs.Windows XP
Go to Start, navigate to Settings and click on Control Panel, navigate to Add or Remove Programs, choose Programs and Features, find Adsupplyads.com related programs, and hit Remove.Windows 7/Vista
Go to Start, navigate to Control Panel, select Uninstall a program/Programs and Features, find Adsupplyads.com related programs, and click on Uninstall.Completely Remove BrowseSmart’s leftover and Registry Files
1. Go to Registry Editor to remove all its related registry entries. Click "Start" button and selecting "Run." Type "regedit" into the box and click "OK." Then you will open up Registry Editor, search for and remove the following registry files of BrowseSmart.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ‘1’
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ‘0’
2. Navigate to directory %PROGRAM_FILES%\ BrowseSmart \ and delete the infected files manually.
%AllUsersProfile%
%AllUsersProfile%\Programs\{random letters}\
%AllUsersProfile%\Application Data\~r
%AllUsersProfile%\Application Data\~dll
Conclusion:
BrowseSmart is not a reputable ad-supported application that has been recognized as harmful adware infection which has the capability to make trouble on common-used browsers, including Internet Explorer, Mozilla Firefox and Google Chrome. As long as being informed of its abnormal symptoms, it is necessary for users to delete it from computer in case of unexpected damage or loss. However, BrowseSmart is similar to many viruses released that can escape antivirus or can even prevent from scanning. Why? It’s obvious that people usually got this virus on their computers when surfing online, but when they wanted to remove it, only to find that the antivirus programs couldn't pick it up at all. This is mainly because BrowseSmart hides deep in the registry entries and mutates at quick speed that is capable of blocking antivirus software. Besides, it can also infect many system files and make them become its associated files. In this case, users may adopt the helpful manual removal to clean up all its components from PC.
Anyhow, manual removal is a high-level process that is only suggested for advanced users. Any mis-operation may lead to worse result. If you cannot handle the operation alone, you may ask help from the recommended VilmaTech 24/7 Online Experts for real-time support.
Thursday, March 13, 2014
Remove VBS/Autorun.worm.aapn!lnk, Get Rid of Worm Infection Easily
VBS/Autorun.worm.aapn!lnk is a new type of network worm infection that is operated by cyber criminals. It is a common computer virus, which mainly makes use of Internet to fulfill its duplication and propagation. Security experts have considering VBS/Autorun.worm.aapn!lnk as an intelligent network worm because it could automatically attack and scan existed system vulnerabilities on a targeted node host upon its installation, and then it will spread its malicious components to other node hosts for widely attack. PC users may get infected with VBS/Autorun.worm.aapn!lnk when they visit malicious websites or open unknown links/attachments embedded in a SPAM email. It is often bundled with some “free” applications which could be downloaded manually from unreliable Internet resources.
Wednesday, March 12, 2014
The ICE Cyber Crime Center Scam Removal, Get Rid of Ransomware Easily
Basic Information of The ICE Cyber Crime Center Virus
The ICE Cyber Crime Center attack annoys numerous computer users as a typical ransomware infection. It is a member coming from the infamous Trojan/Win32.Reveton family. Similar as other ransom virus, The ICE Cyber Crime Center infection is a specific malware produced by cyber criminals to make damage on targeted machine and benefit from victims. To get more knowledge about ICE virus, it will typically render a victim’s computer inoperable with the aid of its advanced screen locker techniques, and then demand users to pay a concoctive forfeit in order for the restriction to be removed. Most commonly, the ransom could be $300 or more, which is required to be paid through MoneyPack or other anonymous online payment system. In order to increase its authenticity, this type of ransomware may claim that the computer is being tracked by law enforcement. Without timely fine paid to the authorities, users may encounter further legitimate sanction.
Monday, March 10, 2014
How to Remove Win64:Dropper-Gen[Drp], Trojan Virus Manual Removal Guides
Does your antivirus pick up the threat - Win64:Dropper-Gen[Drp], but cannot get rid of? What is Win64:Dropper-Gen[Drp] exactly? How dangerous it is? How can I remove Win64:Dropper-Gen[Drp] effectively and safely? No worries, this tutorial will show you how to remove Win64:Dropper-Gen[Drp] step by step. Read more.
File name:C:\\Windows\explorer.exe
Severity: High
Status: Threat:Win64:Dropper-Gen[Drp]

File name:C:\\Windows\explorer.exe
Severity: High
Status: Threat:Win64:Dropper-Gen[Drp]

Thursday, March 6, 2014
How to Remove JS:Decode-BTB [Trj] with Manual Skills
JS:Decode-BTB [Trj] is a new type of Trojan infection designed by cyber criminals to make hazards on affected computer and gain from victims. Most commonly this type of infection can always invade a targeted machine without any permission or knowledge. By using advanced social engineering tactics, JS:Decode-BTB [Trj] is often distributed by some “free” downloads from unreliable online resources containing the activations code of the virus. When users download or update those specific applications, JS:Decode-BTB [Trj] could be directly dropped and installed on users’ computer.


Wednesday, March 5, 2014
How to Remove Us.yhs4.search.yahoo.com, Latest Browser Hijack Virus Removal

Us.yhs4.search.yahoo.com (http://us.yhs4.search.yahoo.com/) is not a reputable domain which has been popularly recognized as a browser hijack virus designed by cyber criminals for illegal purpose. Most commonly Us.yhs4.search.yahoo.com virus sneaks into a targeted machine with dishonest approaches without user’s authorization or knowledge. To be specific, this type of browser hijack virus is always bundled with some “free” applications’ downloads. When users download those malignant programs, the Us.yhs4.search.yahoo.com virus could be installed and executed on compromised computer automatically. Moreover, Us.yhs4.search.yahoo.com may be propagated by some malicious websites or other standard web pages that have been assaulted by the developers of virus. In addition, computer users may infected with with Us.yhs4.search.yahoo.com when they open unknown attachments or links embedded in a SPAM email.
Monday, March 3, 2014
Remove Cryptorbit Ransomware, How to Decrypt Your Personal Files
Recently numerous computer users are stuck with “Cryptorbit” which cannot get rid of. What is Cryptorbit exactly? Is the alert announced by Cryptorbit real? How to remove Cryptorbit threat from computer effectively? No worries, this tutorial will teach you how to eradicate Cryptorbit step by step. Read more.
Cryptorbit is a newly released malware that is categorized as ranosmware infection, mainly aiming at individuals. This type of ransomware is a hack tool designed by cyber criminals for kid napping, which is similar as the Council of Europe Scam virus. Basically, Cryptorbit ransom virus could permeate into a targeted machine easily with the help of its advanced SEO techniques. To be specific, malware distributors may spread the activation code of Cryptorbit virus on some malicious websites or other legitimate web pages that have been compromised. When users click on those infected URLs, the infection could invade computer without any permission or knowledge. Meanwhile, Cryptorbit ransomware may be also packaged with some “free” applications’ downloads that seem to be standard for users. Once being installed, Cryptorbit ransom will forcibly restrict the access to Windows that it infects while encrypting user’s personal files on affected machine. These may include videos, photos and documents.
What is Cryptorbit?
Cryptorbit is a newly released malware that is categorized as ranosmware infection, mainly aiming at individuals. This type of ransomware is a hack tool designed by cyber criminals for kid napping, which is similar as the Council of Europe Scam virus. Basically, Cryptorbit ransom virus could permeate into a targeted machine easily with the help of its advanced SEO techniques. To be specific, malware distributors may spread the activation code of Cryptorbit virus on some malicious websites or other legitimate web pages that have been compromised. When users click on those infected URLs, the infection could invade computer without any permission or knowledge. Meanwhile, Cryptorbit ransomware may be also packaged with some “free” applications’ downloads that seem to be standard for users. Once being installed, Cryptorbit ransom will forcibly restrict the access to Windows that it infects while encrypting user’s personal files on affected machine. These may include videos, photos and documents.
How to Remove Win32:BHO-ALX[Trj], Easy Way to Delete Trojan Virus

Win32:BHO-ALX[Trj] is a malicious PC infection that is designed to corrupt targeted computers and benefit from victims. Most commonly Win32:BHO-ALX[Trj] is promoted by some free downloads from unreliable Internet resources. Computer users may get infected with this type of infection when navigating to a malign link embedded in SPAM email or visiting compromised websites that contain the activation code of the virus. When installed, it will modify default system configuration such as Windows boot sector by technically implanting its codes. Thereupon Win32:BHO-ALX[Trj] virus could be executed automatically whenever Windows boots up. Stealthy as Win32:BHO-ALX[Trj] virus is, it may slow down the performance of affected computer through taking up high computing resources. Besides, serves as a vicious JavaScript, Win32:BHO-ALX[Trj] threat may redirects search queries while users utilize search engines, including Yahoo, Google or Bing. It is certain that computer users are obliged to get rid of Win32:BHO-ALX[Trj] infection from computer as long as being noticed of its existence. Otherwise, it may even open part of system to third party and lead to further compromise by other attackers. This will directly cause worse results on affected computer.
Thursday, February 27, 2014
How to Remove LNK:FakeFolder-B [Trj], Latest Trojan Virus Manual Removal
What is LNK:FakeFolder-B [Trj]?

Wednesday, February 26, 2014
Way to Remove Safe Saver Pop-Up, Latest Manual Removal Guides
Why does Safe Saver pop-ups keep displaying on my screen? What are Safe Saver pop-ups? How do I get rid of Safe Saver pop-ups effectively? No worries, this post will resolve your problem completely. Read more.
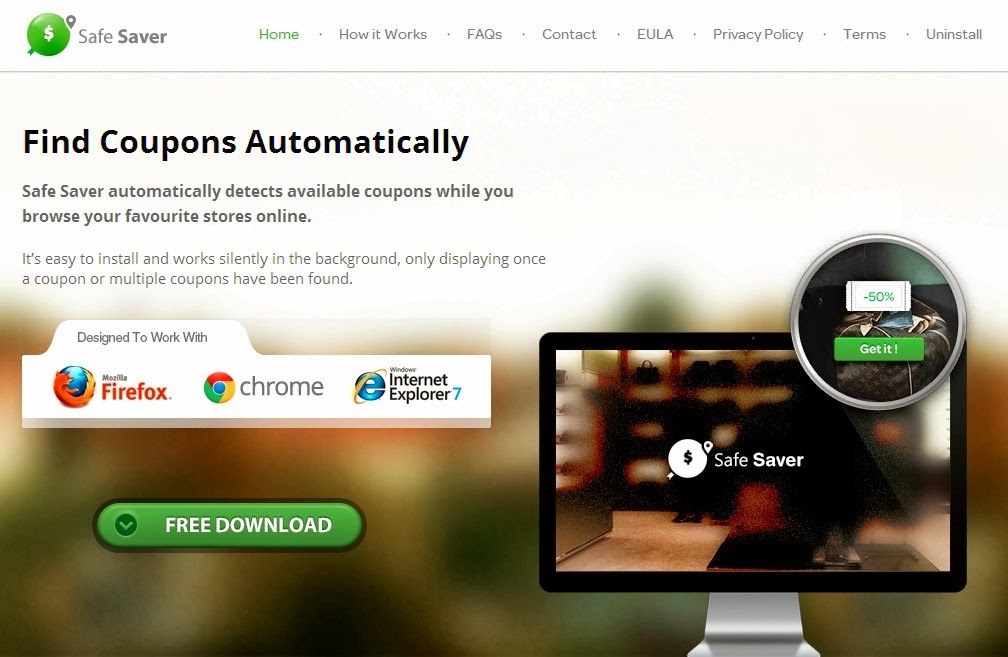
Safe Saver claims to be a practical web browser auxiliary tool which has the capability to automatically provide homologous coupons pertaining to user’s browsing routine. In reality, Safe Saver cannot be definitely classified as a virus or spyware. However, according to its existing attributes, it can be distinguished as a PUP (potentially unwanted program) that may be harmful for user’s computer.
What is Safe Saver?

Safe Saver claims to be a practical web browser auxiliary tool which has the capability to automatically provide homologous coupons pertaining to user’s browsing routine. In reality, Safe Saver cannot be definitely classified as a virus or spyware. However, according to its existing attributes, it can be distinguished as a PUP (potentially unwanted program) that may be harmful for user’s computer.
Sunday, February 23, 2014
Search.easylifeapp.com Removal, How to Remove Easylifeapp Search Hijack Virus
Search.easylifeapp.comredirect virus mess up your browser? Is your homepage stuck with http://search.easylifeapp.com/?chplbf=1 that you cannot get rid of? No worries, this post will show you how to get rid of Search.easylifeapp.com redirect virus completely.
Search.easylifeapp.com, also known as Easylifeapp.com or Easylifeapp Search, has been classified as a browser hijack virus which has the capability to bring about website traffic on popular-used browsers, regardless of IE/Firefox/Chrome. According to the recent security statistics, Search.easylifeapp.com virus is believed to be spread using various social engineering tactics. To be specific, this type of threat is commonly distributed by malicious websites or other legitimate web pages that have been assaulted by the developers of virus. Meanwhile, tricky as Search.easylifeapp.com virus is, it is often packaged with specific application produced by cyber criminals that seems to be standard for users. In addition, this browser hijack virus may be also propagated by unknown email that contains infected attachments or links.
Information of Search.easylifeapp.com
Search.easylifeapp.com, also known as Easylifeapp.com or Easylifeapp Search, has been classified as a browser hijack virus which has the capability to bring about website traffic on popular-used browsers, regardless of IE/Firefox/Chrome. According to the recent security statistics, Search.easylifeapp.com virus is believed to be spread using various social engineering tactics. To be specific, this type of threat is commonly distributed by malicious websites or other legitimate web pages that have been assaulted by the developers of virus. Meanwhile, tricky as Search.easylifeapp.com virus is, it is often packaged with specific application produced by cyber criminals that seems to be standard for users. In addition, this browser hijack virus may be also propagated by unknown email that contains infected attachments or links.
Friday, February 21, 2014
Council of Europe Scam Removal, How to Get rid of Linkup Ransomware
Your web browser is locked by Council of Europe ransomware? How dangerous Council of Europe virus is? How to completely get rid of Council of Europe scam? No worries, this post will show you how to terminate Council of Europe virus from computer for good. Read more.
Council of Europe, or so-called Linkup ransomware, is a new type of web browser locker infection that is designed by cyber criminals to make destruction on affected operating system and ultimately benefit from victims. According the resent security reports, the Council of Europe virus is commonly prompted via drive-by-download that often happens surreptitiously. To be specific, this type of infected may be lurked onto a targeted machine when users visit malicious websites or legitimate web pages that have been compromised. In addition, Council of Europe ransomware may be spread with the aid of Trojan horse or other destructive PC threats which has the capability to take advantage of system vulnerabilities to drop and install the components of Council of Europe virus. When executed, Council of Europe ransomware will immediately replicate its codes and registry files so that to make chaos in kernel system.
What is Council of Europe?
Council of Europe, or so-called Linkup ransomware, is a new type of web browser locker infection that is designed by cyber criminals to make destruction on affected operating system and ultimately benefit from victims. According the resent security reports, the Council of Europe virus is commonly prompted via drive-by-download that often happens surreptitiously. To be specific, this type of infected may be lurked onto a targeted machine when users visit malicious websites or legitimate web pages that have been compromised. In addition, Council of Europe ransomware may be spread with the aid of Trojan horse or other destructive PC threats which has the capability to take advantage of system vulnerabilities to drop and install the components of Council of Europe virus. When executed, Council of Europe ransomware will immediately replicate its codes and registry files so that to make chaos in kernel system.
Wednesday, February 19, 2014
Remove Cdn.optmd.com Pop-up, Adware Manual Removal Guides

Cdn.optmd.com meddles with Internet user’s online routine by forcibly displaying numerous pop-up advertisements on affected web browser, despite of Internet Explorer, Mozilla Firefox and Google Chrome. Cdn.optmd.com has been classified as a malware that is linked to adware or browser hijack virus. Usually, computer users may get infected this malady when they visit malicious websites or other compromised web pages containing the activation code of the virus. Meanwhile, this infection is also distributed by specific programs that pretend to be legitimate applications. When users download and install the malign program onto computer, the Cdn.optmd.com can be directly activated in system without any permission or knowledge.
Monday, February 17, 2014
Remove Windows AntiBreach Tool, Get Rid of Rogue Virus Effectively
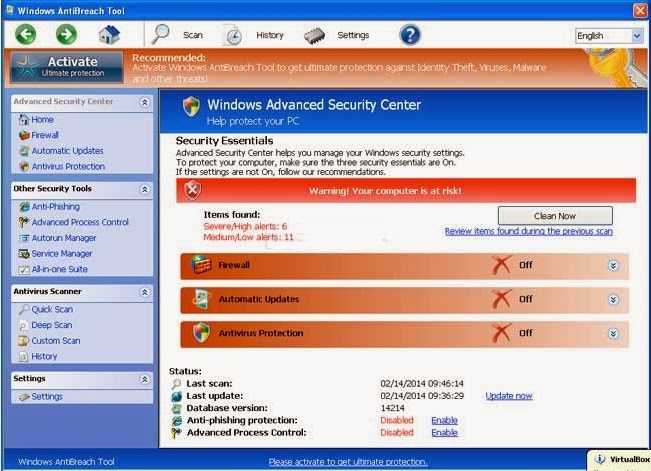
Friday, February 14, 2014
Way to Remove Win32:BProtect-D [Trj], Uninstall Trojan Virus From Windows
What is Win32:BProtect-D [Trj]?

In computers, Win32:BProtect-D [Trj] is a malicious program utilized by cyber criminals to make chaos on targeted operating system. Up to now, Win32:BProtect-D [Trj] is capable of assaulting Windows 7, XP, Vista and Windows 8 OS. Most commonly Win32:BProtect-D [Trj] is distributed by malign websites or legitimate web pages that have compromised to the developers of malware. Another common-used way to spread this type of infection is attacked email containing attachments or links. Furthermore, computer users may get infected with this malady when they download certain “free” application online that contains the activation code of the virus. When executed, Win32:BProtect-D [Trj] may immediately insert its vicious codes and files in order to mess up kernel system. As a result, Win32:BProtect-D [Trj] may make affected computer sluggish by taking up high system resources. In addition, suppose Win32:BProtect-D [Trj] cannot be removed from PC timely, it may exploit found system loopholes to install additional threats to do further harm on kernel system. Thereupon to avoid unwanted damage or loss, it is obligatory to eradicate Win32:BProtect-D [Trj] from system as long as being noticed of its alert.
Thursday, February 13, 2014
How to Remove JS:Iframe-DHY [Trj], Manual Removal Guides
How to Recognize JS:Iframe-DHY [Trj] Infection
1. JS:Iframe-DHY [Trj] attacks system without any permission
2. JS:Iframe-DHY [Trj] reputation & rating online is terrible
3. JS:Iframe-DHY [Trj] may hijack, redirect and modify your web browser
4. J JS:Iframe-DHY [Trj]violates your privacy and compromises your security
More Information of JS:Iframe-DHY [Trj]

Wednesday, February 12, 2014
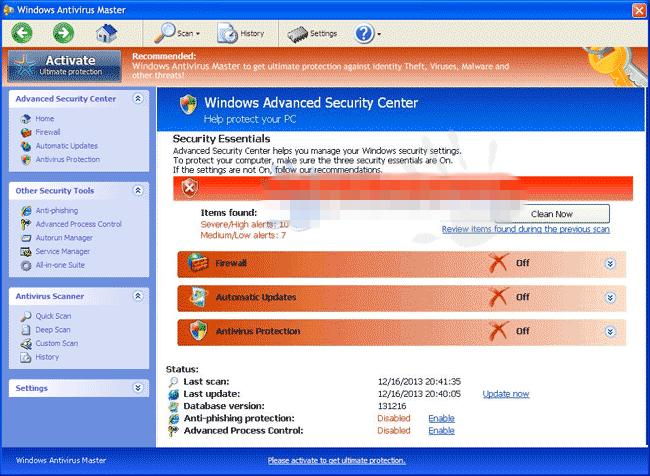
Learn to Remove Windows Antivirus Master, Rogue Virus Manual Removal
Tuesday, February 11, 2014
Remove Svchost.exe Virus Easily, Manual Removal For Windows
Overview of Svchost.exe
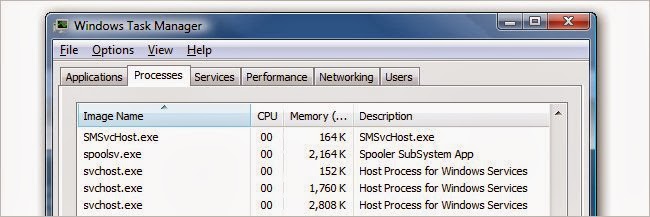
Svchost.exe serves as a kernel system process that hosts multiple Windows services maintaining the regular work of operating system. It is also known as Service Host, or SvcHost that is generally implemented as dynamically-linked libraries (DLLs). The Svchost.exe file is located in c:\windows\system32 or c:\winnt\system32 directories according to the specific version of Windows. Generally, computer users are able to view the work of Svchost.exe through Windows Task Manager. Each Svchost.exe process may take control of a certain program or a group of services. As a result, it is not suggested to end up the process of Svchost.exe without definite requirement.
Saturday, February 8, 2014
Simple Way to Remove Trojan horse Dropper.Generic9.SLV, Manual Removal
Recently numerous computer users get a problem of Trojan horse Dropper.Generic9.SLV detected by antivirus application such as AVG, Norton or MSE. Though this type of Trojan virus may be quarantined or removed by antivirus software, it may still come back over and over again after PC reboots. In reality, Trojan horse Dropper.Generic9.SLV is a new hack tool designed by cyber criminals to make damage on affected computer and gain from victims.
Friday, February 7, 2014
Remove JS:Redirector-BOS [Trj] Thread, Guide to Eradicate Trojan Virus
Example of Detected JS:Redirector-BOS [Trj]
URL: http://tracker.irc.su/scrape?info_hash
Infection: JS:Redirector-BOS [Trj]
Process: C:\Users\Owner\...\BitTorrent.exe
Overview of JS:Redirector-BOS [Trj]
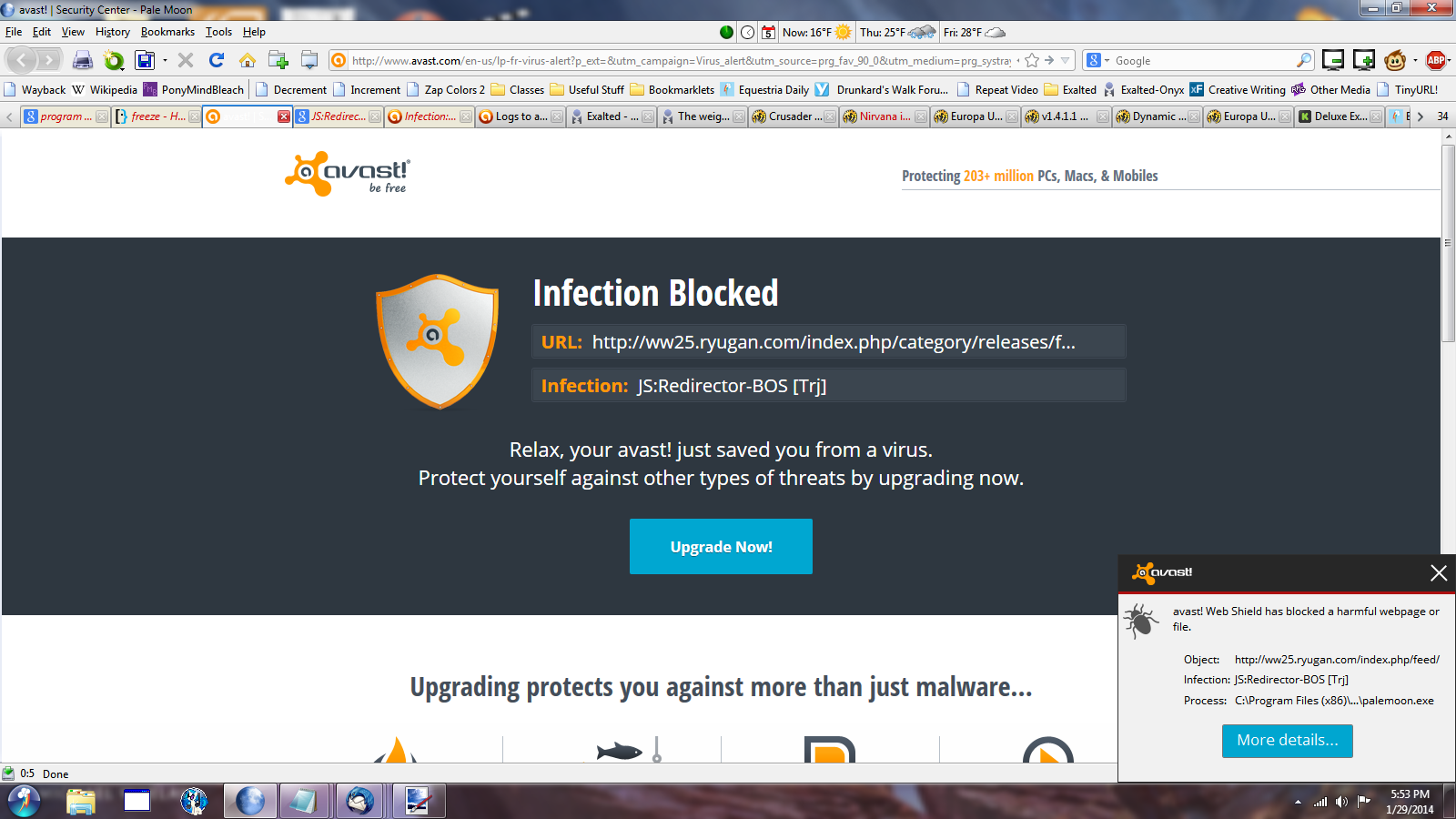
JS:Redirector-BOS [Trj] is a freshly destructive PC infection that has been reported by some popular-used antivirus programs such as AVAST and MalwareBytes. The thread has the capability to take control of PC’s Internet connection to generate web traffic and make other unexpected damage on affected PC forcibly. Most commonly PC users may realize the notification of JS:Redirector-BOS [Trj] every few second when they running Bittorrent or visiting certain websites. In reality, the blocked URL or other object may not be malicious, but is only assaulted and utilized by JS:Redirector-BOS [Trj] threat.
Monday, February 3, 2014
Remove Snap.do Virus, Toolbar/Redirect Virus Manual Removal Instruction
Snap.do is a series of product developed by Resoft Inc. which claims to provide the perfect web browser tool such as Snap.do toolbar or other plugins to enrich Internet users’ online experience. However, according to the complaint of numerous Internet users, Snap.do has been recognized as a malign browser hijack virus which meddles with user’s regular activities. To be specific, Snap.do may often permeate onto a victim’s computer without any permission or knowledge. This may happen when Internet users visit malicious websites or some standard web pages that have been assaulted by the virus. Moreover, Snap.do is frequently bundled with some freeware or share applications that seem to be legitimate for computer users. As long as users download and install those infected programs onto computer, the Snap.do infection can be directly activated and executed automatically.

Sunday, February 2, 2014
Trojan: Win64/Patched.H, How to Remove
Trojan: Win64/Patched.H is a newly released PC infection which should be terminated from computer as long as being informed of its existence. Basically, this type of Trojan infection cannot replicate its components by itself to spread onto a victim’s computer. Most commonly, Trojan: Win64/Patched.H may be bundled with some freeware or shareware online downloads. When Internet users install the infected computer, the Trojan: Win64/Patched.H virus can be activated and executed automatically. Up to now, this Trojan virus has been caught by numerous standard antivirus applications such as McAfee, Microsoft Security Essentials, AVGfree or Norton.
Wednesday, January 29, 2014
Remove VirTool:Win32/Obfuscator.XZ, Helpful Manual Removal Guides
Computer runs weird when the VirTool:Win32/Obfuscator.XZ malware is activated. What is VirTool:Win32/Obfuscator.XZ exactly? Since antivirus or antispyware didn't help to get rid of VirTool:Win32/Obfuscator.XZ virus, you should take some effective manual removal steps to ensure it is gone absolutely. This post will teach you how to get rid of VirTool:Win32/Obfuscator.XZ effectively. Read more.
VirTool:Win32/Obfuscator.XZ is a specific Trojan infection which has been reported by numerous antivirus applications such as Microsoft Security Essentials, Kaspersky, MalwareBytes. However, being endowed with hiding techniques, VirTool:Win32/Obfuscator.XZ virus can generally escape the regular detection and removal of antivirus software programs. Most commonly this type of virus mainly attacks Windows operating system especially those are short of proper system security protection.
What is VirTool:Win32/Obfuscator.XZ
VirTool:Win32/Obfuscator.XZ is a specific Trojan infection which has been reported by numerous antivirus applications such as Microsoft Security Essentials, Kaspersky, MalwareBytes. However, being endowed with hiding techniques, VirTool:Win32/Obfuscator.XZ virus can generally escape the regular detection and removal of antivirus software programs. Most commonly this type of virus mainly attacks Windows operating system especially those are short of proper system security protection.
Monday, January 27, 2014
Metropolitan British Police Scam Removal, How to Remove Ransomware Infection
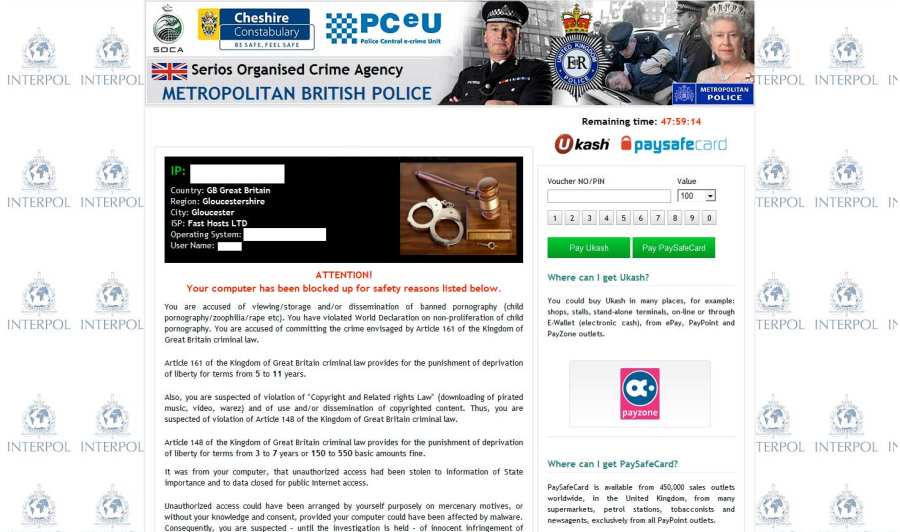
Metropolitan British Police virus is another typical PC locked virus which mainly attacks the PC users who are living in United Kingdom. VilmaTech Computer Experts have classified Metropolitan British Police virus as a destructive ransomware infection which has the capability to generate unexpected destruction on the affected operating system. Specifically, this type of malware generally blocks access to target computer with its advanced screen locker techniques. While rendering the machine inaccessible, Metropolitan British Police virus will display a bogus notification on the monitor, claiming that the computer has been locked on the ground of violation against the local law. To unlock computer and avert from further punishment, the infection will threaten users to pay a imaginary fine through anonymous online payment system.
Subscribe to:
Comments (Atom)













